Failover Policy Control
Topic
This article describes the Failover Policy Control feature of the Datto Networking Appliance (DNA).
Environment
- Datto Networking Appliance (DNA)
Description
The Failover Policy Control feature allows an operator to interrupt existing sessions for LAN clients during transitions to and from 4G LTE failover, and to specify the manner in which the DNA interrupts the sessions.
To access the Failover Policy Control card, log into the DNA web interface, and click Firewall, as shown in Figure 1.
Procedure
1. Click the Failover Policy Control option in the Networks pane.

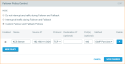
Figure 2: Failover Policy Control
2. You will see the configuration card shown in Figure 3.
The Failover Policy Control card allows you select from the following interruption methods:
- Do not interrupt any traffic during Failover and Failback: The DNA will not interrupt any traffic when a failover transition occurs. In this mode, some traffic may have issues recovering, while other traffic will be able to resume, depending on the specific protocol and applications involved. VPN tunnels created or configured through the DNA will continue to function during failover transition and operation. This mode may use LTE data without alerting the administrator.
- Interrupt all traffic during Failover and Failback: The DNA will interrupt all network traffic when a failover transition occurs (via ICMP Port Unreachable for UDP, TCP Reset for TCP).
- Custom Failover and Failback Policies: When this option is selected, the DNA will interrupt only the traffic coming from the specified Source IP via the specified Protocol for each enabled rule, using a pre-defined Method. The available interruption methods are:
- ICMP Port Unreachable
- TCP Reset
- ICMP Net Unreachable
- ICMP Host Unreachable
- ICMP Protocol Unreachable
- ICMP Net Prohibited
- ICMP Host Prohibited
Select the interruption method most applicable to your environment.
You can increase the granularity of the rule's control by adding a specific Destination IP and range of Ports. This allows you to create rules such as:
- "When this rule is enabled, interrupt only the traffic coming from this Source IP using this protocol by using this interruption method."
- "When this rule is enabled, interrupt only the traffic coming from this Source IP using this protocol and going to this IP by using this interruption method."
- "When this rule is enabled, interrupt only the traffic coming from this Source IP using this protocol to these ports by using this interruption method."
- "When this rule is enabled, interrupt only the traffic coming from this Source IP using this protocol and going to this IP to these ports by using this interruption method."